Create Security Group
In this step, we will create the security groups used for our instances. These security groups specify to the VPC which connections are allowed or permitted. A security group acts as a virtual firewall that controls traffic for one or more instances. By default, AWS allows all outbound traffic but restricts inbound traffic. We only config the directions inbound in this lab.
I. Create security group for public subnet
Inbound rules:
| ID | Connection Types | Sources | Ports |
|---|---|---|---|
| 1. | Ping (ICMP - IPv4) | 0.0.0.0/0 (anywhere) | |
| 2. | SSH | 0.0.0.0/0 (anywhere) | |
| 3. | UDP (IPsec) | 0.0.0.0/0 (anywhere) | 500 |
| 4. | UDP (IPsec) | 0.0.0.0/0 (anywhere) | 4500 |
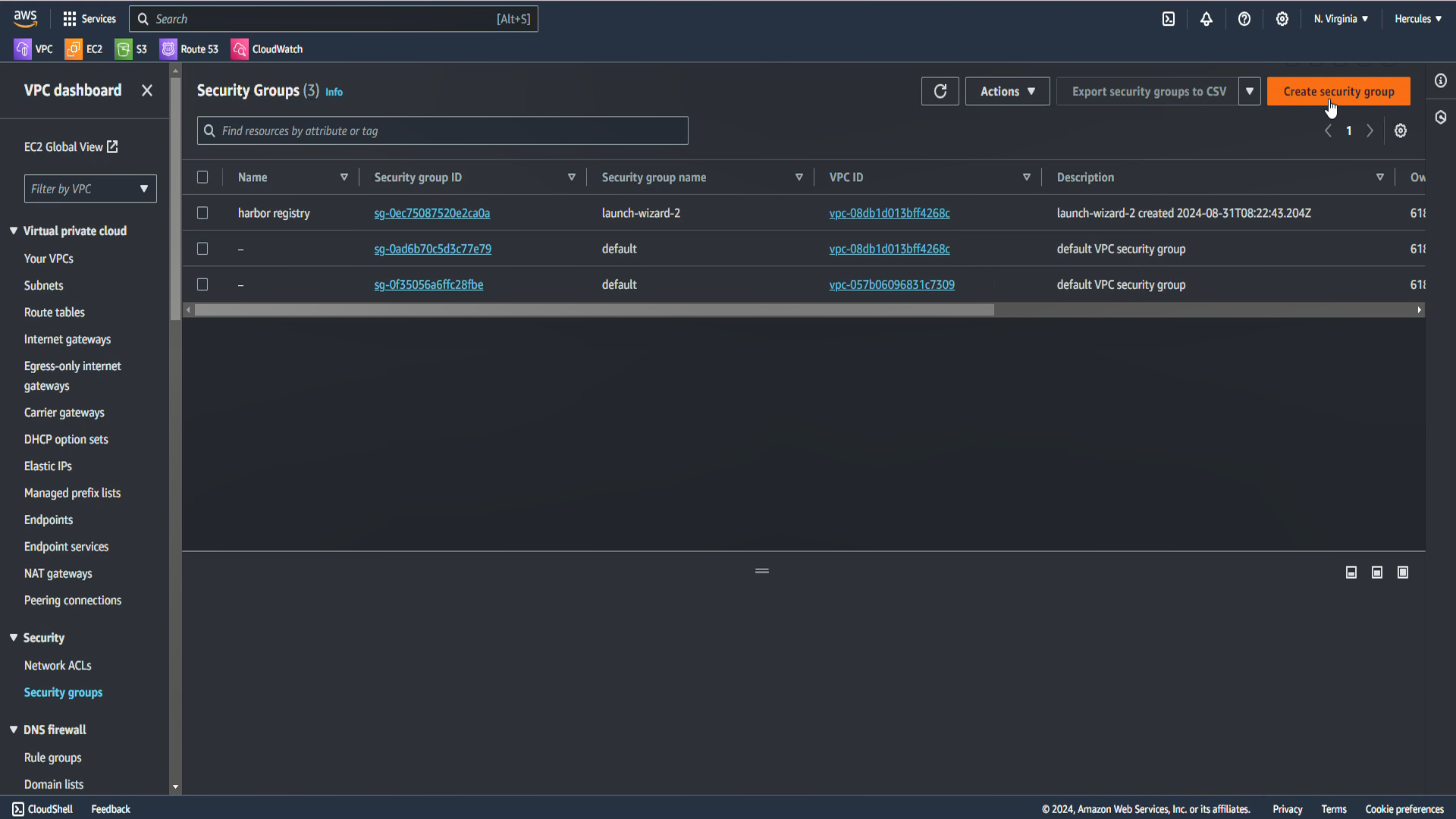
- Go to VPC Dashboard
- Click Security Group.
- Click Create security group.
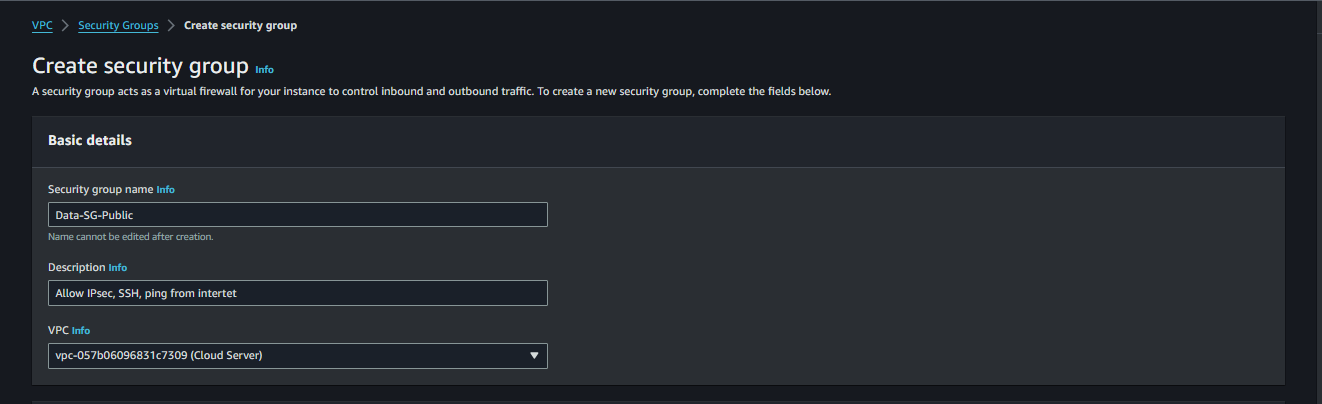
- In the Security group name section, enter
Data-SG-Public.- In the Description section, enter
Allow IPSec, SSH, ping from internet. - In the VPC section, select the Data Server VPC.
- In the Description section, enter
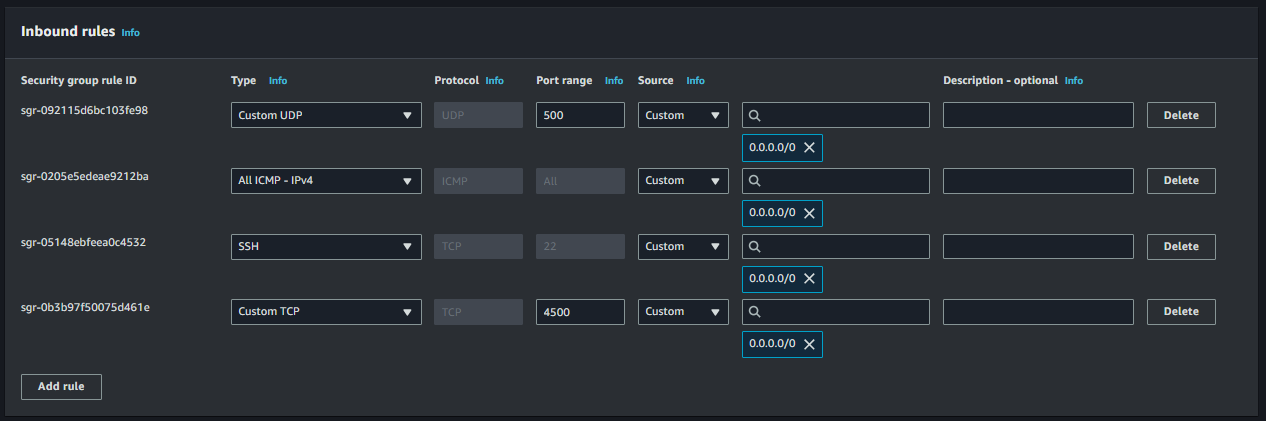
Config Inbound rules
Allow ping connection, choose Add rule:
- In the Type section, choose Custom ICMP - IPv4 to allow ping from IPv4.
- In the Source type section, select Anywhere - IPv4.
Allow SSH connection, choose Add rule:
- In the Type section, choose SSH.
- In the Source type section, select Anywhere - IPv4 to allow SSH from internet.
Allow UDP (IPSec) connection, choose Add rule:
- In the Type section, choose Custom UDP to allow ping from IPv4.
- In the Port range section, enter the port
500to allow ping from IPv4. - In the Source type section, select Anywhere - IPv4 to allow VPN connection from internet.
Do the same with UDP port
500, we create UDP port4500.And we keep Outbound rules as the default.
Scroll down at the bottom of page and click at Create security group, so we have finished creating the necessary security groups for the EC2 instances.
You can find more information about How does IPsec work? and IPsec protocol port in VPN connection.